Demystifying the Network Security Key Everything You Need to Know

In today’s increasingly interconnected world, network security has become a paramount concern for individuals and businesses alike. At the heart of protecting our digital assets lies the key, a fundamental component in safeguarding our networks from unauthorized access and potential cyber threats. However, understanding and effectively managing this crucial element of can often be a daunting task for many. This article aims to demystify the network security key, providing a comprehensive overview of its importance, functions, and best practices for ensuring a robust and secure network environment. Whether you are a novice user or an experienced IT professional, this guide will equip you with everything you need to know about keys and enable you to enhance the security of your network infrastructure.
Demystifying the Network Security Key Everything You Need to Know
In today’s digital age, is of utmost importance. With the increasing number of connected devices and the rise of cyber threats, protecting your network is crucial. One essential aspect of is the key. In this article, we will delve into everything you need to know about this key and how it is used to secure your network.
What is a Network Security Key?
A key, also known as a Wi-Fi password or passphrase, is a sequence of characters used to authenticate and encrypt data transmitted over a wireless network. It acts as a barrier, preventing unauthorized access to your network and ensuring that only authorized devices can connect.
Why is a Network Security Key Important?
The key plays a vital role in maintaining the security and integrity of your network. Without a secure key, anyone within the range of your Wi-Fi signal can potentially connect to your network and gain access to your sensitive information. This leaves you vulnerable to various cyber threats such as data breaches and identity theft.
How is a Network Security Key Generated?
A key is typically generated automatically when setting up a wireless network. It can be a combination of letters, numbers, and special characters, making it harder for unauthorized users to guess or crack. The length and complexity of the key can greatly impact the security of your network. It is recommended to use a strong, unique password for each network to enhance security.
There are primarily two types of keys: WEP (Wired Equivalent Privacy) and WPA (Wi-Fi Protected Access).
WEP: WEP was the first encryption protocol introduced for wireless networks. However, it is now considered outdated and insecure. WEP keys can be easily cracked by attackers using readily available tools.
WPA: WPA is the successor to WEP and offers stronger security. There are two versions of WPA: WPA-Personal and WPA-Enterprise.
WPA-Personal: WPA-Personal, also known as WPA2-PSK (Pre-Shared Key), is the most commonly used encryption method for home and small office networks. It requires users to enter a key or passphrase to connect.
WPA-Enterprise: WPA-Enterprise, also known as WPA2-Enterprise, is primarily used in larger organizations. It utilizes an authentication server, such as RADIUS (Remote Authentication Dial-In User Service), for user authentication, adding an extra layer of security.
How to Change Your Network Security Key?
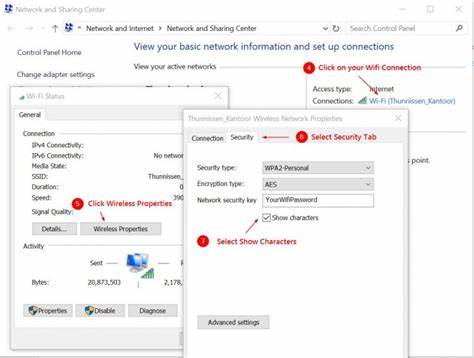
Changing your key periodically is a good practice to enhance the security of your network. To change your key, you need to access your router’s settings page. This can usually be done by typing the router’s IP address into a web browser and entering the administrator username and password. From the settings page, locate the wireless security settings and change the key to a new, strong password.
The key is a crucial component of . It acts as a gatekeeper, ensuring that only authorized devices can connect to your network. By choosing a strong, unique key and periodically changing it, you can significantly enhance the security of your network and protect your sensitive information from potential cyber threats.